Android certificates
To intercept a device's network you need to install a certificate into it, this certificate grants a third-party application permission to record/intercept other application requests, but there's two types of certificates: user-trusted and system-trusted certificates.
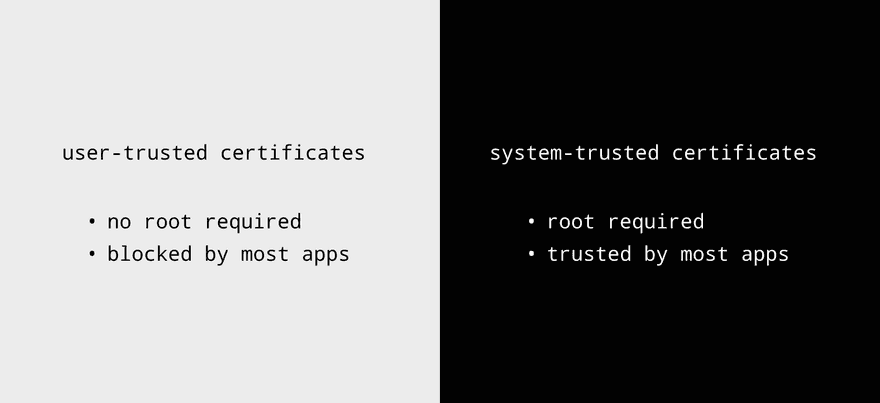
User-trusted certificates, as the name implies, are installed by the user and they are blocked by almost every android app (except some old applications). Basically any device (with root or not) can install a user-trusted certificate, but they are not useful 90% of the times, so this is not what we are looking for.
System-trusted certificates, are built-in thus trusted by the system and most installed android applications (even so, some very strict applications may block it either). Although it's much easier to intercept requests by installing these kind of certificates, you need root access to install it.
But there is no need to start downloading a modified ROM for your device neither searching for tutorials to unlock your bootloader.
Android Studio emulators
Here is where emulators come to play, you can use Android Studio emulators instead of your device, specifically emulators without Google Play Services. These emulators are rooted by default, so you don't need to root your real phone to start tracking app requests.
Install it on their website: https://developer.android.com/studio/.
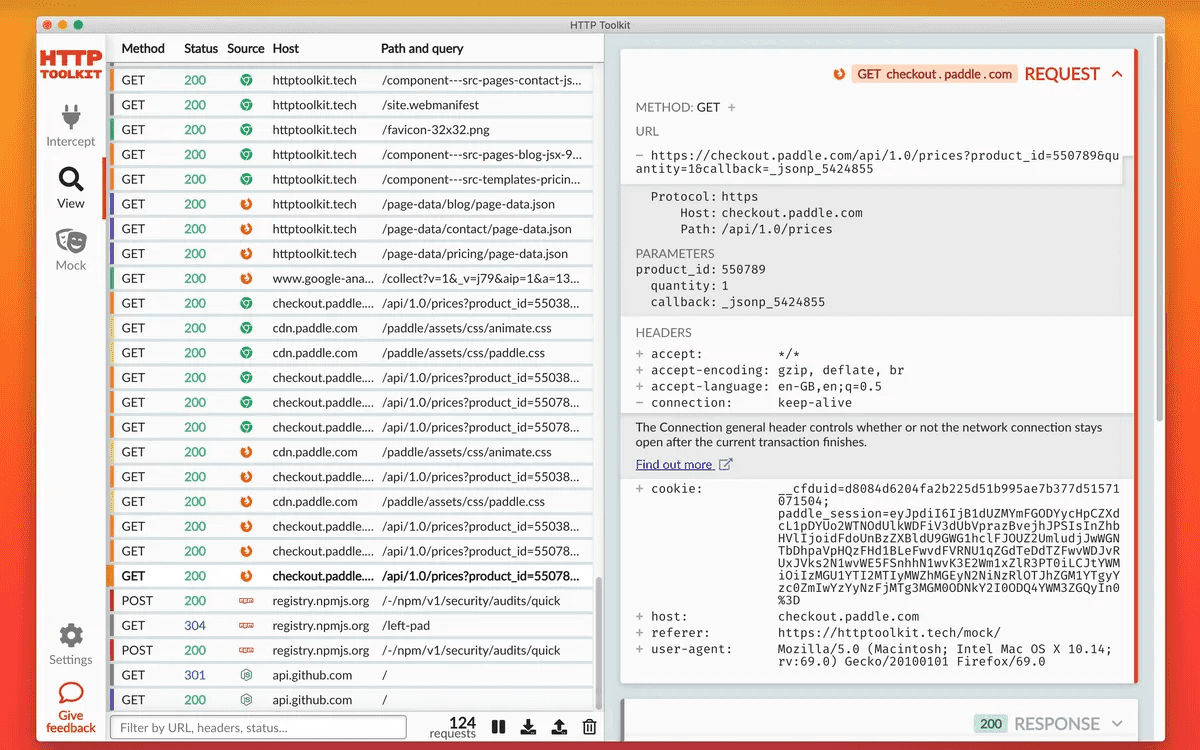
HTTP Toolkit
Another tool you can also use is the HTTP Toolkit, it allows you intercept traffic not only from android but any live being that supports the TCP.
Install it on their website https://httptoolkit.com/.